Computerworld reports that Microsoft has said it will issue an emergency patch for the critical Windows shortcut bug on Monday, Aug. 2.... The company said that it is satisfied with the quality of the "out-of-band" update -- Microsoft's term for a patch that falls outside the usual monthly delivery schedule -- but also acknowledged that it has tracked an upswing in attacks.
As this is an extremely serious bug, users need to make sure that this patch gets installed on their PC.
Friday, July 30, 2010
Thursday, July 29, 2010
Fake Firefox Flash Update is Rogue
PC Magazine is reporting that F-Secure has uncovered the latest in rogue anti-malware: A fake Firefox "Just Updated" page which pushes you to install an update to Flash. Don't fall victim to rogue software. Make sure that you control what get's installed on your computer.
Sunday, July 25, 2010
Digital Forensics Association Research Report: Five Years of Data Breaches
A new report from the Digital Forensics Association confirms the need for organizations to pay careful attention to all aspects of information security.The report "The Leaking Vault - Five Years of Data Breaches" analyzes over 2,800 data loss incidents from publicly accessible sources, with a known disclosure of 271.9 million records. This study—the largest of its kind to date—provides analysis on which breach vectors carry the most risk, and should help provide organizations with more accurate information when combating this problem.
Key findings include:
Key findings include:
- Business, government, educational and medical organizations have been responsible for losing on average over 395,000 people's data per day every day for five years.
- Hacking was responsible for 45% of all exposed records with an average loss of 716,000 records
- Stolen laptops were responsible for 49% of breaches but only 6% of lost records per incident.
- The fastest growing attack vector is social engineering
- Social Security Numbers (SSNs) are the most frequent data element reported.
- The Business sector accounted for 70% of breach incidents
Friday, July 23, 2010
Spyware Targets Industrial Facilities, including SCADA systems
Following up our blog post of last week in which we described new malware attacks on industrial control systems, the Christian Science Monitor writes "cyberspies have launched the first publicly known global attack aimed at infiltrating hard-to-penetrate computer control systems used to manage factory robots, refineries, and the electric power grid."
According to the Monitor, "the spyware had spread for at least a month undetected and has already penetrated thousands of industrial computer systems in Iran, Indonesia, India, Ecuador, the United States, Pakistan, and Taiwan, according to a Microsoft analysis. ... The attack is part of a sophisticated new wave of industrial cyberespionage that can infiltrate corporate systems undetected and capture the "crown jewels" of corporations – proprietary manufacturing techniques that are worth billions, experts say. It's significant, too, because of its potential to infiltrate and commandeer important infrastructure, such as the power grid."
The Monitor goes on to write "No one knows who's behind it. Cybersecurity analysts aren't even sure yet what the spyware's creators intend it to do to those industrial systems. The intent could be to sell corporate proprietary secrets – or to seek an advantage over the US in some future assymetric conflict, such as a cyberwar."
According to the Monitor, "the spyware had spread for at least a month undetected and has already penetrated thousands of industrial computer systems in Iran, Indonesia, India, Ecuador, the United States, Pakistan, and Taiwan, according to a Microsoft analysis. ... The attack is part of a sophisticated new wave of industrial cyberespionage that can infiltrate corporate systems undetected and capture the "crown jewels" of corporations – proprietary manufacturing techniques that are worth billions, experts say. It's significant, too, because of its potential to infiltrate and commandeer important infrastructure, such as the power grid."
The Monitor goes on to write "No one knows who's behind it. Cybersecurity analysts aren't even sure yet what the spyware's creators intend it to do to those industrial systems. The intent could be to sell corporate proprietary secrets – or to seek an advantage over the US in some future assymetric conflict, such as a cyberwar."
Monday, July 19, 2010
CyberSecurity Threat Indicator Raised as Critical Windows Zero-Day Vulnerability Discovered
Computerworld and other sources are reporting a newly-discovered critical bug in all versions of Windows. The bug is so critical that the Internet Storm Center (ISC) has pushed its Infocon threat indicator to "Yellow," a rare move, while Symantec also bumped up the status of its ThreatCon barometer to "Elevated." Users are being warned to expect widespread attacks.
"The proof-of-concept exploit is publicly available, and the issue is not easy to fix until Microsoft issues a patch," said Lenny Zeltser, an ISC security analyst.
Last Friday, Microsoft confirmed that attackers can use a malicious shortcut file, identified by the ".lnk" extension, to automatically execute their malware by getting users to view the contents of a folder containing such a shortcut. Malware can also automatically execute on many systems when a USB drive is plugged into the PC.
All versions of Windows, including the just-released beta of Windows 7 Service Pack 1 (SP1), as well as the recently retired Windows XP SP2 and Windows 2000, contain the bug.
In a related post, we reported that Sieman is warning customers about attacks on its industrial control software that exploit this bug.
"The proof-of-concept exploit is publicly available, and the issue is not easy to fix until Microsoft issues a patch," said Lenny Zeltser, an ISC security analyst.
Last Friday, Microsoft confirmed that attackers can use a malicious shortcut file, identified by the ".lnk" extension, to automatically execute their malware by getting users to view the contents of a folder containing such a shortcut. Malware can also automatically execute on many systems when a USB drive is plugged into the PC.
All versions of Windows, including the just-released beta of Windows 7 Service Pack 1 (SP1), as well as the recently retired Windows XP SP2 and Windows 2000, contain the bug.
In a related post, we reported that Sieman is warning customers about attacks on its industrial control software that exploit this bug.
Friday, July 16, 2010
New Malware Targets Industrial Control Systems, like SCADA
PCWorld reports that Siemens is warning customers of new and highly sophisticated malware targeting the computers used to manage large-scale industrial control systems used by manufacturing and utility companies [SCADA]. The malicious software is designed to infiltrate the systems used to run factories and parts of the critical infrastructure. The zero-day malware targets Siemens management software called Simatic WinCC, using a previously undisclosed Windows bug to break into the system.
Tuesday, July 13, 2010
Microsoft Security Updates ... Support Ends for XP, Service Pack 2
KrebsOn Security.com reports "Microsoft today released software updates to fix at least five security vulnerabilities in computers running its Windows operating system and Office applications.... Four out of five of the flaws fixed in today’s patch batch earned a “critical” rating, Redmond’s most severe. Chief among them is a bug in the Help and Support Center on Windows XP and Server 2003 systems that’s currently being exploited by crooks to break into vulnerable machines."
In related Microsoft security news, today also marks the planned end-of-life deadline for Windows XP Service Pack 2, a bundle of security updates and features that Microsoft first released in 2004.Microsoft will no longer support this product, so if you haven't already done so, it's time to upgrade to at least SP3.
In related Microsoft security news, today also marks the planned end-of-life deadline for Windows XP Service Pack 2, a bundle of security updates and features that Microsoft first released in 2004.Microsoft will no longer support this product, so if you haven't already done so, it's time to upgrade to at least SP3.
Monday, July 5, 2010
Microsoft Warns of Uptick in Attacks on Unpatched Windows Flaw
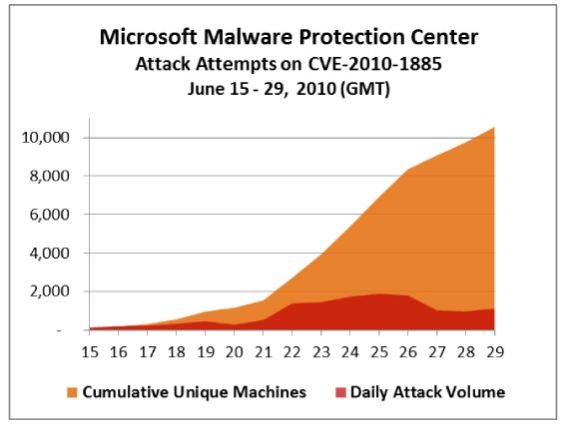
KrebsOnSecurity reports "Microsoft is warning that hackers have ramped up attacks against an unpatched, critical security hole in computers powered by Windows XP and Server 2003 operating systems. The software giant says it is working on an official patch to fix the flaw, but in the meantime it is urging users to apply an interim workaround to disable the vulnerable component." Microsoft issued a statement last week saying the pace of attacks against Windows users had picked up, and that more than 10,000 distinct computers have reported seeing this attack at least one time.
The following graphic from Krebs' blog shows both the daily number of attacks and the cumulative distinct PCs being attacked. As can be seen, peak attacks occurred during the six days from June 22 until June 27.
IT Departments running Windows XP or Server 2003 need to consider running Microsoft’s stopgap “FixIt” tool to disable the vulnerable Help Center component. Users running Windows XP should consider doing this as well. To do so, click this link, then click the “FixIt” button in the middle of the page under the “enable this fix” heading.
The following graphic from Krebs' blog shows both the daily number of attacks and the cumulative distinct PCs being attacked. As can be seen, peak attacks occurred during the six days from June 22 until June 27.
IT Departments running Windows XP or Server 2003 need to consider running Microsoft’s stopgap “FixIt” tool to disable the vulnerable Help Center component. Users running Windows XP should consider doing this as well. To do so, click this link, then click the “FixIt” button in the middle of the page under the “enable this fix” heading.
Subscribe to:
Posts (Atom)